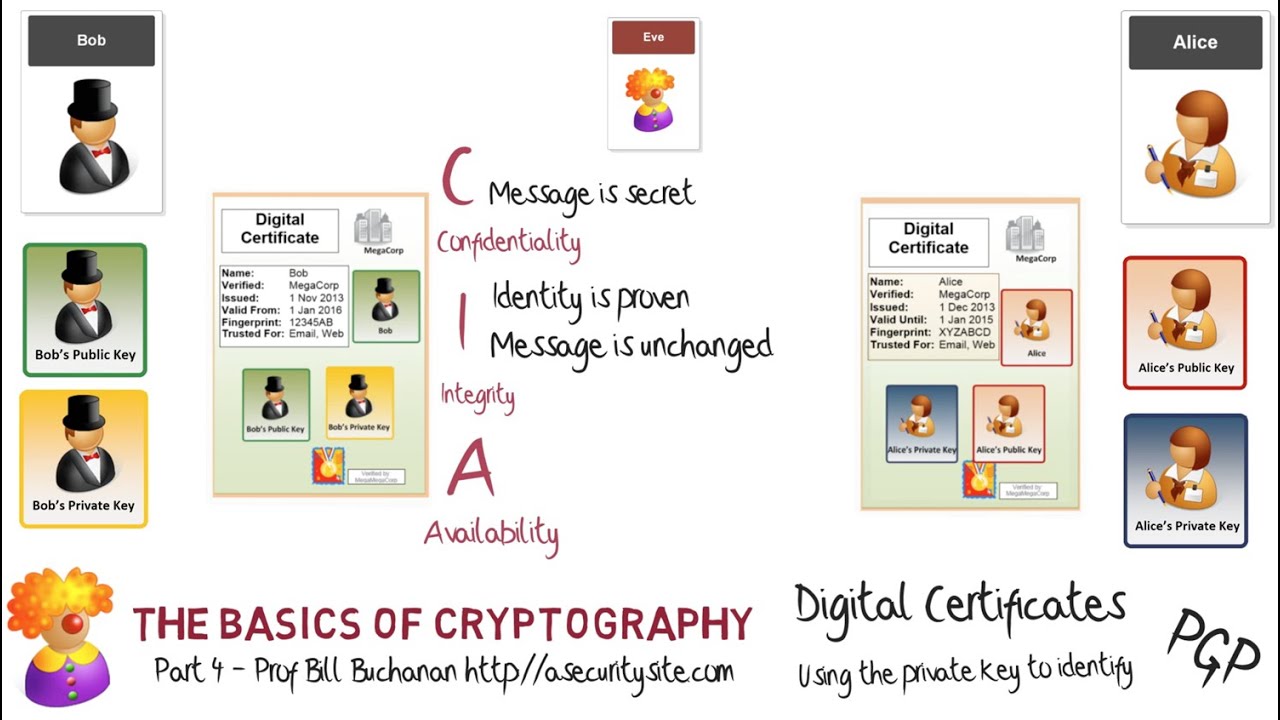
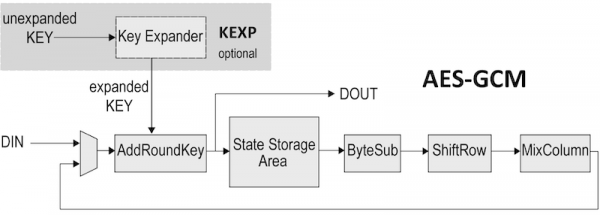
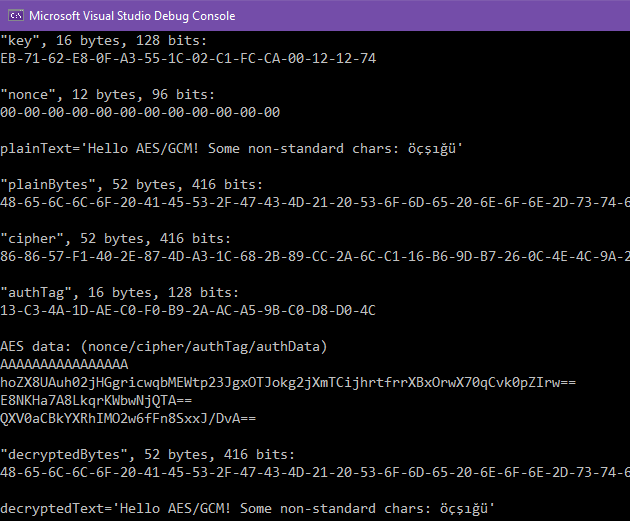
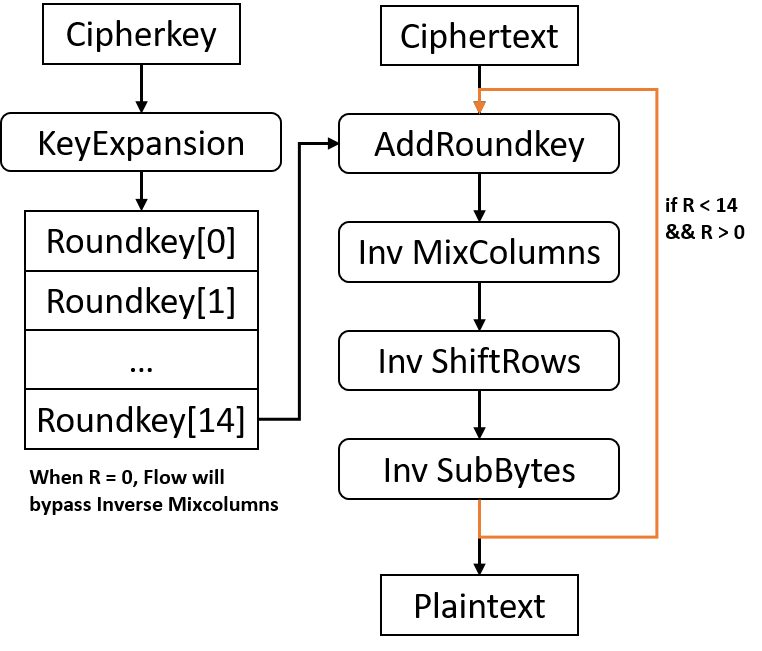
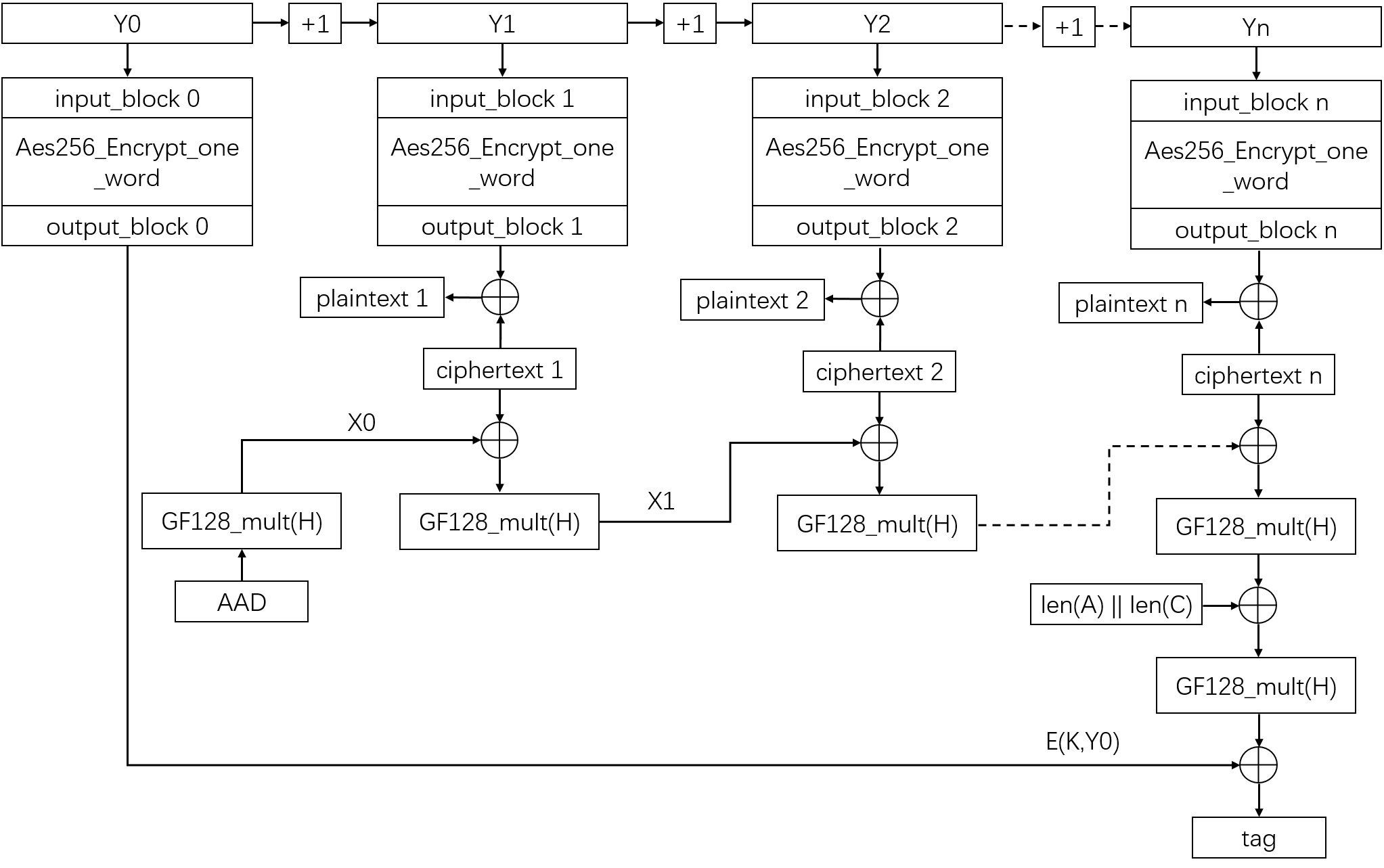
The AES-GCM architecture for an authenticated encryption operation of a... | Download Scientific Diagram

Implementation of AES-GCM encryption algorithm for high performance and low power architecture Using FPGA | Semantic Scholar
Online Cipher Algorithms, Encryption Decryption using aes,aes /cbc/nopadding,blowfish,camellia,cast5,cast6,chacha,des,desede,gcm,gost28147,shacal-2,skipjack,sm4,serpent,shacal2,tea,threefish-1024,threefish-256,threefish-512,tnepres,twofish,vmpc,vmpc ...
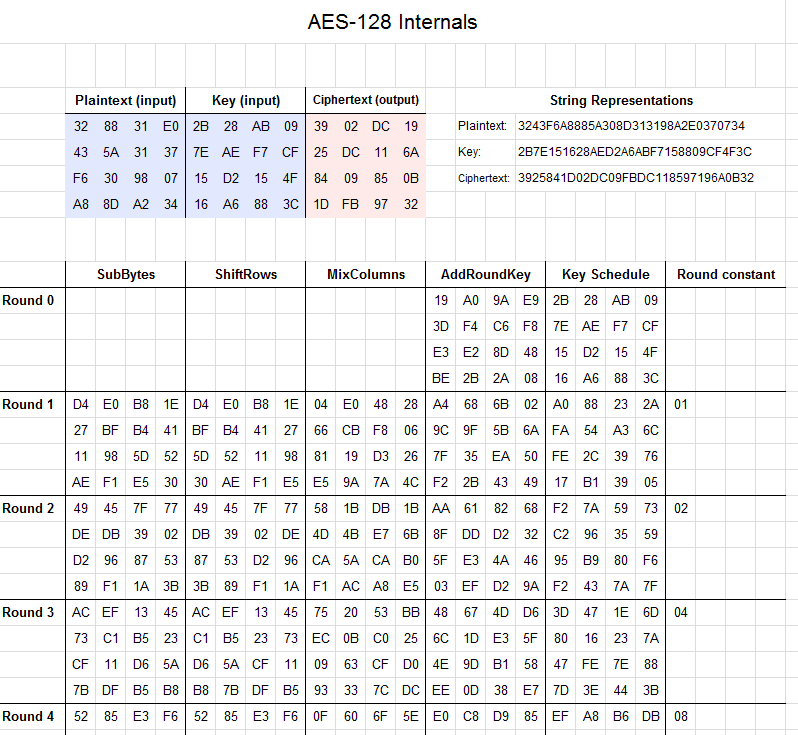
AES Encryption Function ontools | AES Encryption Free Online Tool Supports 128 192 256 Bits... | #1 BEST - AES Encryption Online - ᐈ AES Encryption and Decryption Online Tool | Online AES Encryption and Decryption function ontools
Security Best Practices: Symmetric Encryption with AES in Java and Android | by Patrick Favre-Bulle | ProAndroidDev





![What Is AES Encryption? [The Definitive Q&A Guide] What Is AES Encryption? [The Definitive Q&A Guide]](https://www.trentonsystems.com/hs-fs/hubfs/1-1.png?width=1920&name=1-1.png)